
Blockchain analytics firm Elliptic has reported that 56.5% of the BTC collected by hackers during the Twitter scam has been sent to two digital currency mixing services—a ChipMixer and Wasabi Wallet.
The hackers are sending their BTC to digital currency mixing services because it makes it nearly impossible for onlookers to locate where they are sending the stolen funds to; this makes it easier for the hackers to liquidate their illicit funds without being detected by law enforcement.
“Mixing services make it challenging, if not impossible, to follow the blockchain money trail any further, preventing investigators from identifying where these funds are spent or cashed-out,” said Elliptic co-founder and Chief Scientist Dr. Tom Robinson. “Similarly, it means that if the funds are subsequently sent to an exchange or other regulated service provider, the businesses would not be able to identify that they came from the Twitter scam.”
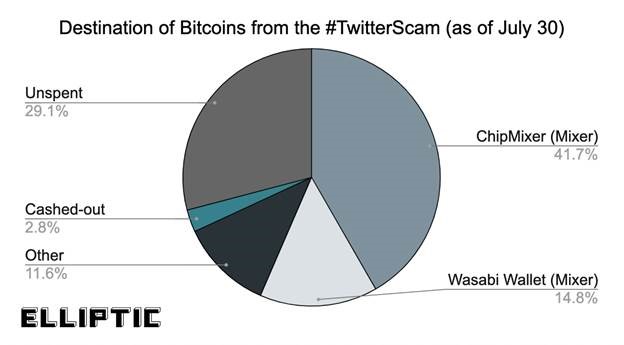
According to Elliptic, a total of 56.5% of the stolen funds has been sent to digital currency mixing services, 2.8% has been cashed out via exchanges, merchants and gambling services, and 40.7% of the stolen BTC remains unspent.
Twitter explains what happened
In an update, Twitter said the attack took place due to very sophisticated social engineer efforts. Twitter says that the hackers targeted Twitter employees to gain access to Twitter’s internal network as well as to obtain employee credentials. Afterward, they used their internal network access and employee credentials to gain access to even more of Twitter’s internal resources, and that the hackers were eventually able to come across the tools that gave them access to every account on Twitter.
“Not all of the employees that were initially targeted had permissions to use account management tools, but the attackers used their credentials to access our internal systems and gain information about our processes,” said Twitter in their update. “This knowledge then enabled them to target additional employees who did have access to our account support tools. Using the credentials of employees with access to these tools, the attackers targeted 130 Twitter accounts, ultimately Tweeting from 45, accessing the DM inbox of 36, and downloading the Twitter Data of 7.”
At least three people have been charged in connection with the Twitter hack. Graham Ivan Clark, 17, was arrested in Florida last July 31 on 30 felony charges, while two other individuals were facing federal charges in California.

 09-22-2024
09-22-2024


