
This post was first published on Medium.
Prove Group Membership Without Ring Signatures
In Part 1, we have demonstrated zk-SNARK turns cryptographic problems into programming problems. As an example, we “programmed” elliptic curve point multiplication to prove knowledge of a private key for a given public key, the equivalent of a digital signature.
Today, we show how to implement another otherwise sophisticated cryptographic primitive by simply “programming” it in zero knowledge language Circom: ring signatures.
Ring Signatures using zk-SNARK
In a ring signature, any member of a group/ring can sign to prove their membership, without disclosing their specific identity. Based on the signature, a verifier can be sure one of the group members signed, but he cannot know which one signed. We have implemented ring signatures before. Even though it is doable, it is far from trivial and requires comprehensive knowledge of cryptography and ingenuity to come up with.
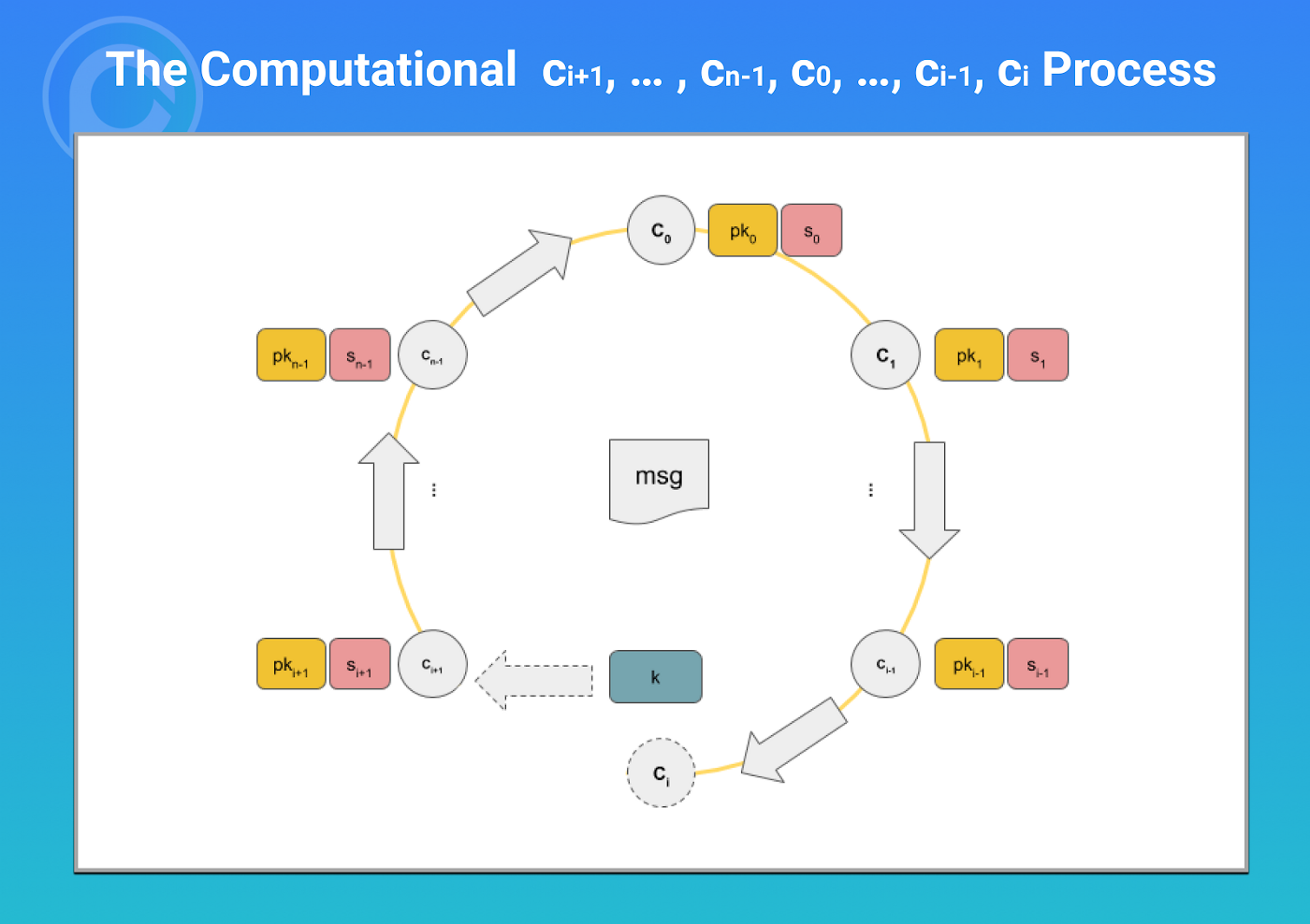
Thanks to the programmability and composability of zk-SNARK, we can simply “coded” ring signature as below, based on the previous point multiplication library.
From Line 11 to 22, we use ECDSAPrivToPub covered in Part 1 to derive a public key at Line 16 from the private key at Line 5 (Note it is declared private)¹. We then just compare the resulting public key with each of the public key in the group defined at Line 7 (Note it is declared public). We return true if and only if it matches any in the group at Line 54.
A test can be found here.
Since the private key input is private and remains hidden, a verifier cannot use it to identify which member created the proof. We have created a ZKP for membership in a group/ring and the equivalent of ring signatures, without knowing any underlying cryptography! This is the power of zk-SNARKs.
***
NOTE:
[1] We prefer ECDSAPrivToPub here over Secp256k1ScalarMult, since it is more efficient.
Watch: The BSV Global Blockchain Convention presentation, Smart Contracts and Computation on BSV
https://www.youtube.com/watch?v=c_zAlkImgTU

 09-20-2024
09-20-2024


