
|
Getting your Trinity Audio player ready... |
McAfee has discovered a new, more sophisticated strain of malware that seeks out cryptocurrency activity.
McAfee Advanced Threat Research (McAfee ATR) has posted that a new, more sophisticated strain of malware has been discovered. This time the malware is far more patient, and far more deadly. And this time it’s looking for bigger fish to catch: Bitcoin users and global banks. It scans for Bitcoin activity and implants itself for long-term data gathering.
According to McAfee ATR, the malware comes from the Lazarus Group, the same notorious cybertheft gang known for the infamous WannaCry ransomware which freezes a user’s computer and threatens to either wipe out its contents or disperse incriminating or humiliating files from the computer unless the owner pays a hefty ransom, usually in bitcoin. The group is also believed to be behind several big-time cryptoheists, as well as multi-million dollar cyberheists instigated against Southeast Asian and European banks.
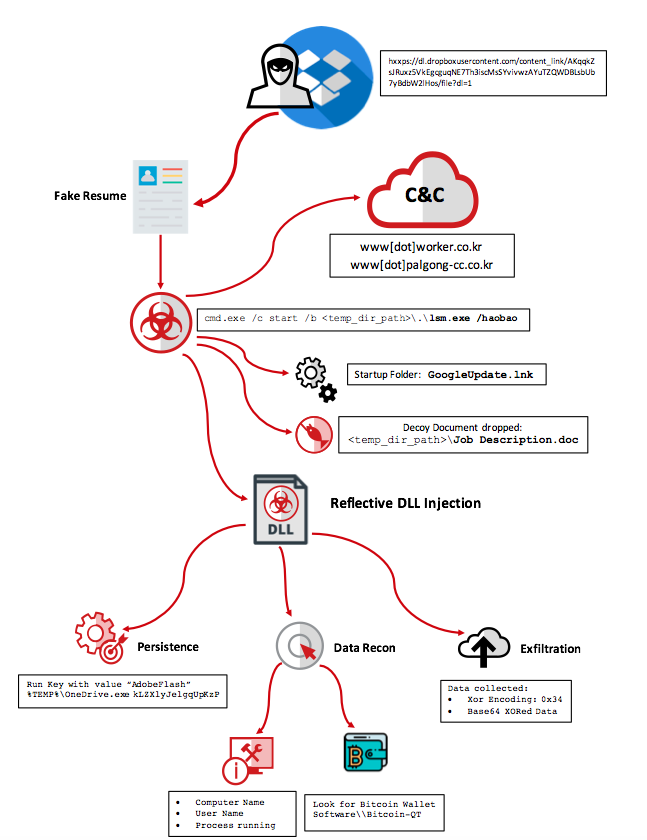
McAfee ATR says that this new malware is a descendant of last month’s phishing email campaign, where a seemingly innocuous Word document containing details of a fake job recruitment is circulated in an attempt to trick users into opening the document.

But the new malware called HaoBao, however, seems to be taking cryptocurrency crime to unprecedented sophistication—its implant is a new breed that was not present in previous Lazarus campaigns.
“McAfee ATR analysis finds the dropped implants have never been seen before in the wild and have not been used in previous Lazarus campaigns from 2017,” Ryan Sherstobitoff wrote for McAfee ATR. “Furthermore, this campaign deploys a one-time data gathering implant that relies upon downloading a second stage to gain persistence. The implants contain a hardcoded word “haobao” that is used as a switch when executing from the Visual Basic macro.”
Despite being only a few years old (as far as we know), the Lazarus Group has been rapidly adding several infamously devastating cyber attacks to their portfolio. Global cybersecurity company Kaspersky Lab has been hunting down Lazarus over the past years since their presence came to light in 2016—they attempted to rob $851 million and managed to run off with $81 million. Kaspersky Lab has been monitoring their modus operandi, and says over 150 malware samples have been attributed to the notorious gang.
Recommended for you
Lorem ipsum odor amet, consectetuer adipiscing elit. Elit torquent maximus natoque viverra cursus maximus felis. Auctor commodo aliquet himenaeos fermentum
Lorem ipsum odor amet, consectetuer adipiscing elit. Accumsan mi at at semper libero pretium justo. Dictum parturient conubia turpis interdum

 11-21-2024
11-21-2024


