
|
Getting your Trinity Audio player ready... |
This post was first published on Medium.
We introduce steganography and explore its potential use cases in the context of Bitcoin.
Steganography
Steganography is a method used to conceal a file (message, image, or video) within another file. The word itself stems from Greek, combining “steganos” (στεγανός), meaning “covered” or “secret,” and “graphein” (γράφειν) meaning “writing.” The main purpose of steganography is to communicate in a way that the existence of the message is kept hidden.
There are various techniques in steganography, ranging from the simple to the complex. Basic methods might involve embedding text within the least significant bits of an image file, where alterations are visually indiscernible to the human eye. More advanced techniques can involve embedding data within audio files, video files, or even the arrangement of words or characters in a text document.
Steganography is used in various fields for secure communication, copyright protection, and even in digital watermarking to track unauthorized file copying.
Steganography has existed for a very long time. Historical tales reveal a unique communication technique from the Roman Empire era: a slave was selected and their head shaved for the purpose of conveying a secret message. Ink was used to tattoo the message onto the bald scalp of the slave. Once the hair had fully regrown, concealing the text, the slave was dispatched to the message’s intended recipient. Upon arrival, the recipient would shave the slave’s head once more to reveal and read the hidden message.

vs. Cryptography
Steganography revolves around concealing the very presence of a message, setting it apart from cryptography. While cryptography encrypts a message to make it unreadable to unauthorized viewers without hiding that a message is being sent, steganography aims to hide the very fact of its existence.
Steganography is most effective when used in conjunction with cryptography rather than as a replacement. This dual approach enables the concealment of the information’s existence as well as the protection of the content itself during storage or transmission. Steganography is almost always encrypted first in practice.
Least Significant Bit Steganography
Least Significant Bit (LSB) steganography is a popular technique used to hide information within an image by manipulating the least significant bits of the pixel values. A carrier image refers to the original image that is used to hide secret data or a hidden message within it, acting as a “cover” or “host” for the hidden data.
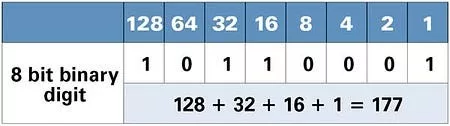
If you were presented with the number $00000000 and given the opportunity to alter just one digit before receiving the amount in cash, it would be unwise to modify the digit farthest to the right, turning it into $00000001. Clearly, adjusting the digit at the far left to make it $10,000,000, or ten million dollars, is far more advantageous than merely obtaining one dollar by changing the digit at the end. Though only a single digit is altered in both scenarios, the digit on the right is deemed the least significant because it impacts the total value the least.
The principle behind LSB steganography is similar and straightforward: it involves replacing the least significant bit(s) of an image’s pixel data with bits of the secret message. In digital images, each pixel’s color is typically represented by a combination of bits for red, green, and blue (RGB) components. The least significant bit is the bit in a byte of data, which has the smallest value or the rightmost bit in a series. This method is popular due to its simplicity and the fact that the changes made to the LSBs of the pixels are usually imperceptible to the human eye, thus maintaining the appearance of the original image while hiding the secret data.
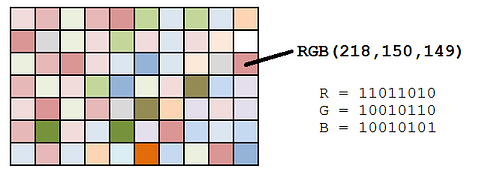
Here’s a basic overview of how LSB steganography works:
- Convert the RGB values of each color channel into binary format.
- For each color channel, extract the four most significant bits (MSBs) from both the carrier image and the hidden image.
- Shift the four MSBs from the hidden image to replace the four least significant bits (LSBs) positions, merging them with the four MSBs of the carrier image.
- Reassemble the RGB channels, forming a new pixel that primarily reflects the carrier image’s MSBs but also encodes the hidden image’s MSBs within its LSBs. This causes a minor alteration in color, making the red box appear slightly more orange due to the embedded information.
Below is an example to hide an image in a cover/carrier image, using 4 least significant bits.

Credit: hide Image 2 in Image 1
To retrieve the hidden message, the recipient, aware of the concealment technique, will reverse the procedure.
- Extract the four LSBs from each pixel of the modified image and shift them to the MSB positions.
- Populate the now-empty LSB positions with zeros (these represent data irretrievably lost in the encoding process).
The concealed image emerges, looking somewhat different from its original due to the LSBs’ data loss, resulting in a slightly darker appearance.
Below is an example.


The two forest images are virtually identical to the human eye while hiding another image.
Potential use cases
In the context of Bitcoin, steganography could protect your crypto assets from theft. It can hide secret information such as private keys, mnemonics, or Bitcoin transactions in an image. It could be beneficial for discreetly storing your seed phrase on paper within your home, making it less likely for a casual burglar to guess what it is. It could also serve well if you need to transport it on yourself through locations where you might undergo searches by individuals intending to confiscate your funds.

You can also disguise secrets within text that appear harmless or inconspicuous.
Stegoseed is a tool to conceal a seed phrase within an ordinary-looking piece of content.

Here are some more innovative examples of using steganography in blockchains.
- skin wallet: store your crypto wallet seed phrase securely & publicly in a tattoo
- AudioStego: put your encrypted private key into an audio track
- StegOnline: create an NFT to store your seed.
Public bounty
The following Ordinal NFT contains a seed phrase with some bitcoins. See if you can crack it and take the bounty. (Note, you must use the original picture here, not the compressed one below).

Watch: Using modern advances in cryptography to enhance data privacy: Owen Vaughan

 11-21-2024
11-21-2024


