|
Getting your Trinity Audio player ready... |
This post was first published on Medium.
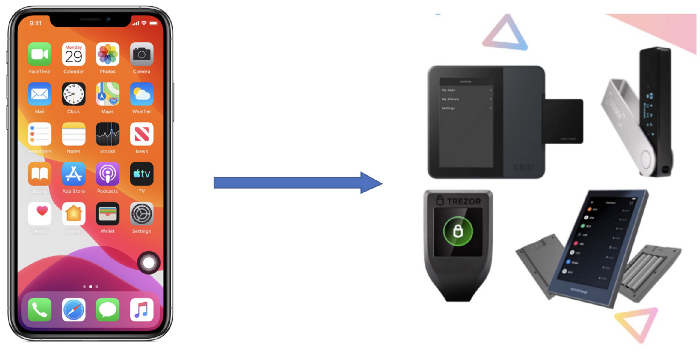
We use the secure enclaves of iOS and Android devices to store Bitcoin private keys. The keys never leave the enclaves, providing same security as hardware wallets. This essentially turns billions of smartphones into secure Bitcoin hardware wallets. Users can authorize Bitcoin transactions using FaceID and TouchID.
Secure Enclave
The Secure Enclave is a special chip in Android, iPhone, iPad and Macs to secure your biometrical data like FaceID and TouchID. The key feature of the Secure Enclave is that a private key generated on it cannot leave the chip, providing maximum security as in hardware wallets such as Ledger and Trezor.
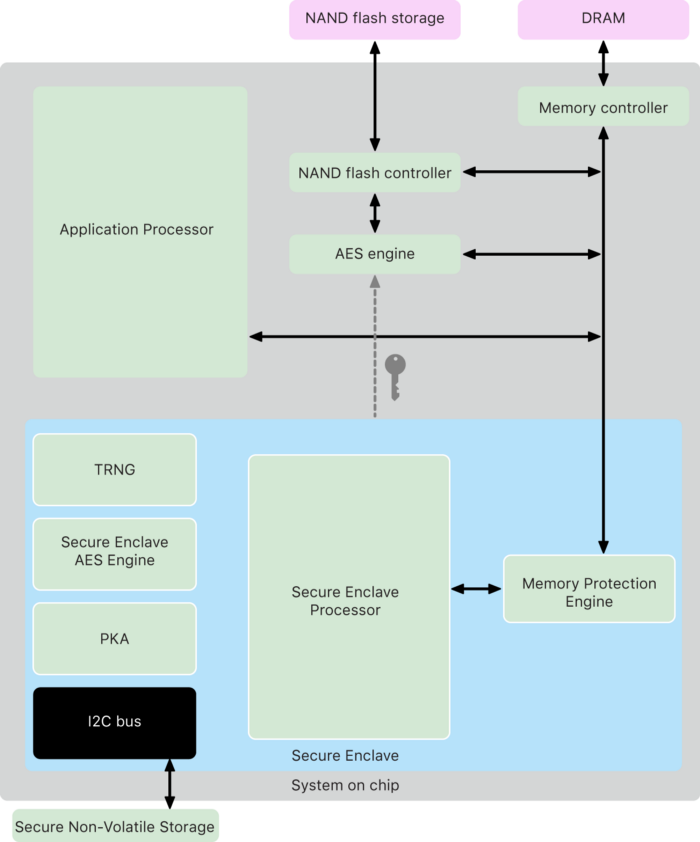

Private key in it can be used to sign messages securely. Messages are sent into the Secure Enclave, signed, and then the signature is returned. The private key during signing reside in the chip and is not stored in memory and thus is inaccessible from software. Permission to sign a transaction can be granted using a biometric authentication such as FaceID and TouchID.
Elliptic curve secp256r1
The Secure Enclave supports a single elliptic curve, secp256r1, also known as prime256 and P-256. It is different from the elliptic curve secp256k1 that’s used for the popular blockchains such as Bitcoin and Ethereum.
Both elliptic curves are of the form y² = x³ + ax + b.
In the secp256k1 curve, we have
a = 0
b = 7
and in the secp256r1 case we have
a = FFFFFFFF 00000001 00000000 00000000 00000000 FFFFFFFF FFFFFFFF FFFFFFFC
b = 5AC635D8 AA3A93E7 B3EBBD55 769886BC 651D06B0 CC53B0F6 3BCE3C3E 27D2604B
Due to the lack of native support of secp256r1, all cryptocurrency wallet apps today are using software signing, instead of hardware signing. Software signing is susceptible to side-channel attacks that leak information about the private key.
Implementing secp256r1 on Bitcoin
Thanks to the expressiveness and scalability of Bitcoin smart contracts, we can implement secp256r1 efficiently, specifically ECDSA signature verification, at contract level. The signature is generated by the Secure Enclave, enjoying maximal security. We then verify the hardware signature in a smart contract. Note this does not require any breaking changes at the base layer, even though it uses a different curve.
We modified the ECDSA verification implementation released before, switching from curve secp256k1 to secp256r1. It basically implements the standard ECDSA verification algorithm.
Backup
To be as secure as possible, the Secure Enclave disallow export keys, making it impossible to backup keys (different from hardware wallets with mnemonic words). If a smartphone is lost and damaged, the private key and the funds it controls are lost.
One solution is to create a 1 of 2 (or N) multisig wallet. One key can be generated offline and safely stored as in a cold wallet. The second key is generated inside the Secure Enclave. In case of phone loss or damage, the user can safely use their offline backup key to move the funds out of the wallet.
Please contact us if you are interested in building the first ever hardware-signing Bitcoin wallet. Some other types of hardware security modules (HSM), which hardware wallets belong to, like Smart Card also support elliptic curves, so they also act as Bitcoin wallets as well.
Watch: Small Payments, Big Fun: Micropayments for Casual Games

 11-21-2024
11-21-2024